-

Why Choose macOS for security: The Advantages of the World’s Most Advanced Desktop Operating System?
What is MacOS? The operating system that Apple created for its Macintosh computers is called macOS. It is an operating system built on the Unix platform and is renowned for […]
-

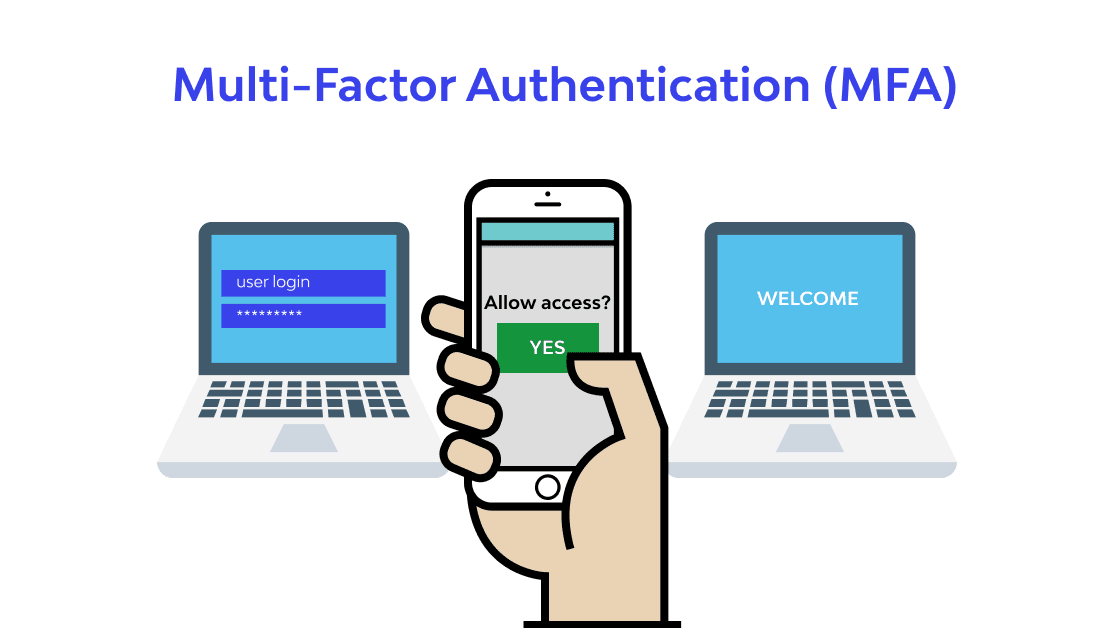
Multi-Factor Authentication (MFA): Bolstering Security with Extra Layers of Digital Protection
What is Multi-Factor Authentication (MFA) ? Multi-Factor Authentication, commonly referred to as 2FA, is an authentication technique that increases security during the login process by forcing users to submit multiple […]
-


Cyber Threats in the Age of Remote Work: Protecting Your Virtual Perimeter
Introduction to Cyber Threats Cyber Threats a malicious act that aims to destroy data, steal data, or otherwise interfere with digital life is referred to as a cyber or cybersecurity […]
-


Cracking the Code: Secure Your Online World with Strong Password Management
What is Password? Before learning about Password Management , first learn about what is Pasword.A password is a secret phrase or group of characters that is used to confirm a […]
-

MacOS Security Checklist: Essential Steps for Safeguarding Your Apple Device and Data
What is MacOS Security Checklist ? A set of precautions are included in a macOS security checklist to protect your Apple machine. It entails using FileVault encryption and a strong […]
-


Software Security for Windows: A Comprehensive Guide to Protecting Your System from Cyberattacks
What is Software? Software is a collection of instructions, information, or programs that are used to run devices and perform certain tasks. Hardware, which is a term for a computer’s […]
-


Elevating Server Performance: The Case for Why Linux is better than Windows
Introduction A server is a piece of computer software or hardware that provides services to other applications or gadgets, also referred to as “clients”. There are many distinct kinds of […]
-

If Your Computer Is Hacked What to Do Window Security:
What is Hacking? Before knowing about what to do when your computer is hacked first of all know about hacking .The act of compromising digital systems and networks by gaining […]
-


The Importance of Cloud Security in the Age of Digital Transformation?
What is Cloud Security? We will know about the importance of cloud security .Cloud security involves preventing unauthorized access to, use of, disclosure of, disruption of, alteration of, or destruction […]

